No Results Found
The page you requested could not be found. Try refining your search, or use the navigation above to locate the post.
Cloud Services
With the evolving concepts of digital twin, digital assets, and the increasing demand of digitalization, Flexinteg offers wide range of services, techniques, and best practices to manage, store, ingest, organize and retrieve data.
This, in turn, makes it easy for the business to scale the solution as user needs change—whether that means increasing the number of licenses to accommodate a growing workforce or expanding and enhancing the applications themselves.
Flexicabos helps organizations transform their IT environment with cost-effective Cloud services. Our team of experts delivers cutting-edge Cloud computing consulting services that help companies boost their productivity to new heights.
Our Cloud managed services make it possible for organizations to reduce their overheads and better productivity, in addition to lowering costs and reducing time-to-market.
We assist customers with our on-demand enterprise Cloud solutions, tools, and applications such as servers, storage, databases, networking, software, and apps, among others.
With our expertise in Cloud managed services, we help our clients become more agile and responsive to the changing market landscape. We help our clients make the right decisions, optimizing their Return on Investment (ROI).
Cloud services are a range of IT applications and resources that include software, infrastructure, and platforms hosted by third-party providers and delivered on-demand to organizations and individual customers through the internet. They can also be referred to as cloud computing; hence the words can be used interchangeably.
Cloud services facilitate the flow of data to and from the servers of cloud service providers/vendors and user/customer servers and gadgets. Users can access cloud services through a computer with an internet connection or a virtual private network. They allow customers to forgo investment into the payment of software licenses and the acquisition of supporting network infrastructure and servers.
The use of cloud services allows our customers to access software, cloud storage, computing power, IT infrastructure, and other services without the need for incurring maintenance costs or carrying out software and hardware updates.
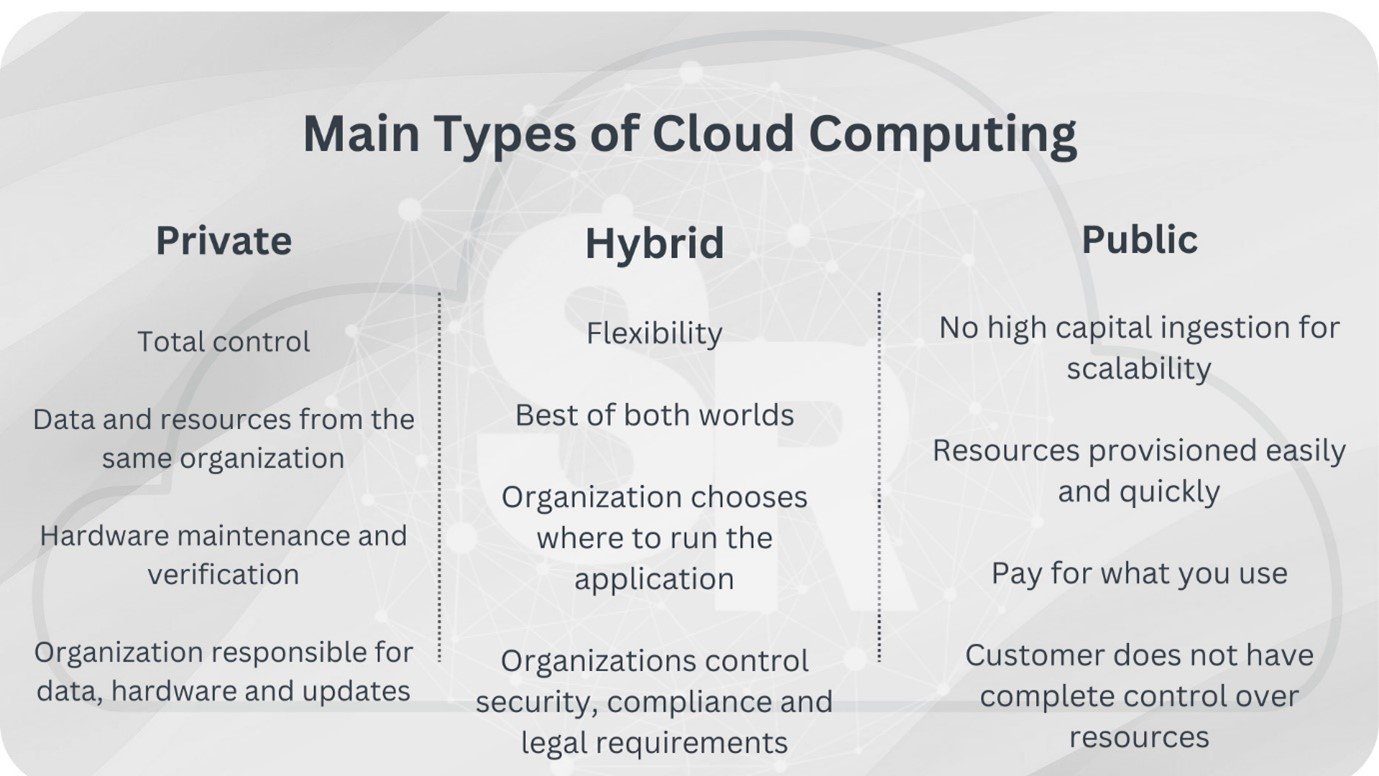
Cloud Deployment Models
Cloud deployment models are premised on virtualization and differ in terms of storage, location, capacity, accessibility, and other facets. The deployment models above are mainly distinguished through the following factors:
BENEFITS OF CLOUD SERVICES
Scalability
Cloud services’ ability to scale as per business needs is an invaluable attribute. It relieves an organization from investment in IT infrastructure resources and software applications as all are provided by a cloud services vendor. Scalability occurs in two ways; increasing user licenses during business booms or enhancing application software to cater to a growing business.
Low Cost
Cloud services allow customers to access cloud storage, application software, and backup facilities without the need to invest in IT hardware and software infrastructure that supports these services and also does away with the need for hardware maintenance and software upgrades.
Instead, users pay an annual or monthly subscription to cloud service providers to access these services. Essentially cloud services convert capital expenditure to operating costs.
Enhanced Flexibility
Organizations enjoy the flexibility to use cloud services when in need only, which reduces costs and at the same time provides assurance of processing capacity to meet demand. If additional resources are no longer needed, organizations can cancel the cloud service subscription.
Data Security
Cloud services are obliged to use the latest and most efficient data security measures due to the large quantity of data handled through their cloud systems. Security of customer data is a prerequisite, as well as being a daily function. Hence, cloud services use security systems that utilize a distributed architecture that can absorb, filter, and deflect malicious requests that pose a threat to the system.